Amazon Linux is a Linux distribution provided by AWS specifically optimized for running workloads on AWS Cloud. This distribution, entirely managed by Amazon teams, offers very high standards in terms of security. In this article I’ll explain why I prefer a Docker image based on Amazon Linux rather than Debian to run a python workload in the cloud.
Debian based Python Docker image
Let’s say you want to create a Docker image to run Python code in version 3.9. Your first choice will probably be to start with a Docker image coming from Docker Hub python:3.9 right? I would have done the same, it’s the easiest way.
Most of the images on the Docker Hub are based on Debian and this is the case for python.
Your Dockerfile would probably look like this :
FROM python:3.9
WORKDIR /usr/src/app
COPY requirements.txt ./
RUN pip install --no-cache-dir -r requirements.txt
COPY . .
CMD [ "python", "./your-daemon-or-script.py" ]Let’s build and push this Docker image to an ECR registry with “Scan on push” enabled. The “Scan on push” feature will run a security scan on your Docker image and see if there are any CVEs in it.
Here is the result of the security scan :
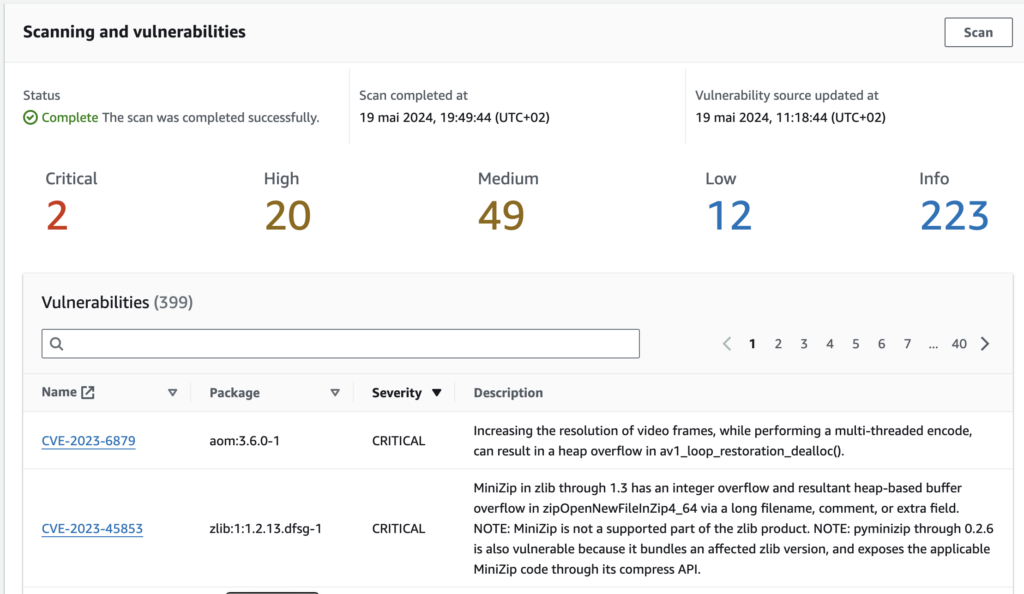
That’s a lot for a fresh image containing only Debian libraries and a bit of python code, isn’t it?
Amazon Linux 2023 based Docker Image
Let’s create a python Docker image now based on amazonlinux:2023 :
FROM amazonlinux:2023
ENV PYTHON_VERSION=3.9
RUN --mount=type=cache,target=/var/cache/dnf \
dnf -y update && \
dnf install -y python${PYTHON_VERSION} python${PYTHON_VERSION}-pip shadow-utils git-all findutils awscli tar && \
update-alternatives --install /usr/bin/python python /usr/bin/python${PYTHON_VERSION} 20 && \
update-alternatives --set python /usr/bin/python${PYTHON_VERSION} && \
dnf clean all
WORKDIR /usr/src/app
COPY requirements.txt ./
RUN pip install --no-cache-dir -r requirements.txt
COPY . .
CMD [ "python", "./your-daemon-or-script.py" ]Here is the result of it’s Security Scan :
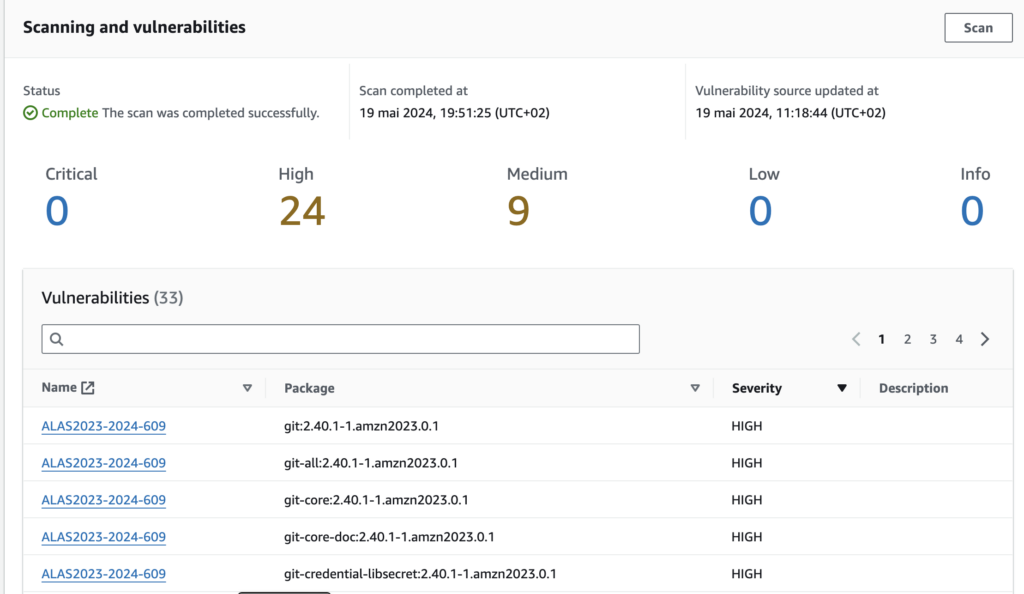
Much better!
Why is there less CVEs in the Amazon Linux image?
The differences in how Debian and Amazon Linux are developed and maintained contribute to the feeling that Debian-based Docker images are less frequently patched and therefore have more unpatched CVEs.
Debian is a community-driven distribution. Security updates for Debian are generally reliable, but the frequency and speed at which they are released can vary because it relies heavily on volunteering contributions.
Python image on Docker Hub is also maintained by community which means that two different communities will have to patch a CVE: the Debian community and the python docker image community
Amazon Linux is a distribution maintained by AWS. Amazon has a dedicated team that prioritizes security updates and patches, often releasing them quickly to ensure that their customers’ systems remain secure.
Amazon’s centralized model and commercially driven approach to maintaining Amazon Linux ensures more consistent and rapid security updates which is why I think it’s better to use docker images based from Amazon Linux instead of Debian.

