Amazon RDS is a very popular choice for creating MySQL databases in the cloud. Many modern companies use it to store their business data. However, as with any other database, securing these databases requires special attention to protect against potential threats and vulnerabilities.
In this article, we will explore 10 best practices for securing your AWS RDS MySQL database instance.
1. Use strong passwords and rotate them
The use of strong passwords is an essential measure to protect your database instance. A strong password consists of a random combination of upper and lower case letters, numbers and special characters. It should be at least 20 characters long.
It is also important to change your password regularly. Passwords should be changed at regular intervals, for example every 60 to 90 days.
Use the MySQL validate_password plugin, which provides additional security like password expiration, password reuse restrictions or password failure tracking.
2. Keep MySQL Updated
One of the major advantages of the managed services offered by AWS is that you don’t have to manage them and can activate automatic updates! It would be silly to do without this… Granted, it doesn’t protect against 0-day flaws, but it’s already very good to protect against known (and patched!) flaws.
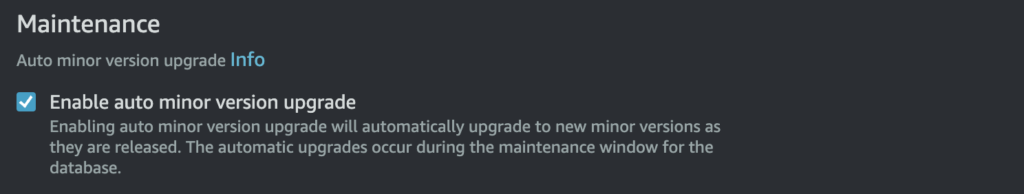
3. Change default port
This good practice protects against bots that regularly scan the internet for instances that are not sufficiently protected. It is very basic but it would be a shame to do without it.
4. Use different users with different permissions
A user should be created for each use. For example, if we have a script that makes backups of our application, we will not use the same user as the application. A read-only user is sufficient here. The root user should only be used to administer the instance, not to use it!
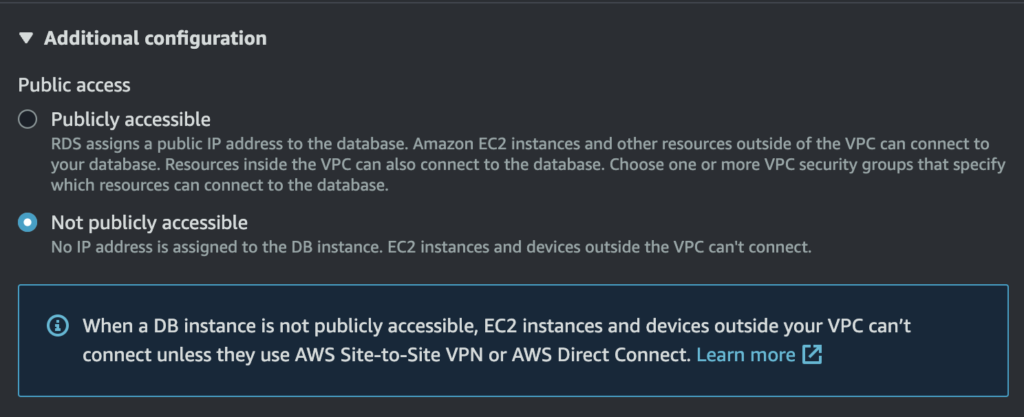
5. Disconnect your RDS instance from the internet
If you have the luxury of being able to disconnect your instance from the internet and make it accessible only from within its VPC network, do it!
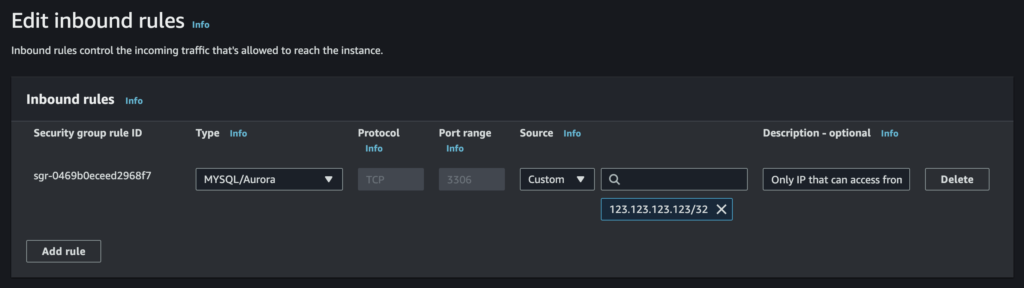
6. Use a Firewall
AWS Security Group can be used to allow only certain IP addresses to connect to your instance’s port :
7. Use MySQL engine host check
Instead of creating your MySQL users like this CREATE USER 'new_user'@'%' IDENTIFIED BY 'password‘; , use MySQL engine host check :
# Fixed IP address
CREATE USER 'new_user'@'123.123.123.123/255.255.255.255' IDENTIFIED BY 'password';
# Private IP range from your subnet
CREATE USER 'new_user'@'192.168.0.0/255.255.255.0' IDENTIFIED BY 'password';8. Use SSL
Implement encryption in transit using SSL :
ALTER USER 'new_user'@'123.123.123.123/255.255.255.255' REQUIRE SSL;9. Grant desired privileges to desired databases
Instead of granting your MySQL user privileges like this GRANT ALL PRIVILEGES ON * . * TO 'new_user'@'123.123.123.123/255.255.255.255'; grant desired privileges to desired databases :
GRANT SELECT, INSERT, UPDATE, DELETE ON my_db.* TO 'some_user'@'123.123.123.123/255.255.255.255';10. Use 2FA or 3FA
MySQL 8.0.27 and higher supports multifactor authentication (MFA), such that accounts can have up to three authentication methods. IAM authentication can also enable multi-factor authentication.

